MIMIC IPMI Protocol Module Guide
-
Table of Contents
-
Overview
The MIMIC IPMI Protocol Module is an optional facility that enables the Intelligent Platform Management Interface (IPMI) Remote Management Control Protocol (RMCP) (full specifications at the official website ). The MIMIC IPMI module simulates the LAN interface and currently implements both the IPMI v1.5 and 2.0 specifications.
Installation
IPMI support is made available in MIMIC as an optional dynamically loadable module. Starting with MIMIC 10.00, you can use the Protocol Wizard to install the IPMI module (select IPMI Simulator). If you prefer to enable IPMI by hand, you need to do the following:
-
Use File->Terminate to stop the any running MIMIC daemon.
-
Copy the IPMI shared library (ipmi.dll on Windows, ipmi.so on Unix)
from "bin/dynamic/optional" to "bin/dynamic" in the
install directory.
-
Install the license keys as detailed in the instructions e-mailed to you.
-
Restart MIMIC.
You should see the following type of message in the MIMICLog that
confirms that the IPMI module was properly loaded :
INFO - IPMI : Loaded protocol from < path-to-DLL > INFO - IPMI v8.00
Once IPMI is loaded, any agent instance configured to support the IPMI protocol will be able to accept IPMI requests from an IPMI application on the "IPMI over LAN" interface.
-
Use File->Terminate to stop the any running MIMIC daemon.
-
Using IPMI from MIMICView
If the IPMI module is enabled, then Agent->Add, Agent->Configure and Agent->Paste dialogs will display IPMI as an additional checkbox in the Advanced pane along with the SNMP protocols. On selecting the checkbox a new IPMI pane will appear.
This IPMI configuration pane lets the user configure the parameters for a IPMI session:
-
Primary Port
This optional parameter specifies an alternate IPMI primary port. The default is the standard port 623.
-
Secure Port
This optional parameter specifies an alternate secure port to use. The default is the standard port 664.
-
Version
This optional parameter specifies the version of the protocol to use, 2.0 or 1.5. The default is 2.0.
-
Primary Port
-
Using IPMI from MIMICShell
A few new commands and some enhanced old commands can be used from the MIMICShell to control the IPMI functionality. Here is a synopsis:
-
mimic protocol msg IPMI get args
This command lets the user gather the self-defining list of arguments required and their particulars. The parameters are detailed above. A sample exchange for this command would be:
mimicsh> mimic protocol msg IPMI get args {{primary_port} {Primary Port} {integer} {} {optional} {623}} {{secure_port} {Secure Port} {integer} {} {optional} {664}} {{version} {Version} {string} {} {optional} {2.0}} -
mimic agent get protocol
This command lets the user look at the protocols currently configured on the agent. A sample exchange for this command would be:
mimicsh> mimic agent get protocol snmpv1,snmpv2c,IPMI
-
mimic agent set protocol
This command lets the user change the protocol setting for an agent. A sample exchange for this command would be:
mimicsh> mimic agent get protocol snmpv1 mimicsh> mimic agent set protocol snmpv1,IPMI mimicsh> mimic agent get protocol snmpv1,IPMI
-
mimic agent protocol msg IPMI get config
This command lets the user get the current argument settings. A sample exchange for this command would be:
mimicsh> mimic agent protocol msg IPMI get config {primary_port=623} {secure_port=664} {version=2.0} -
mimic agent protocol msg IPMI set config [config]
This command lets the user change the current argument settings of all IPMI sessions for an agent. A sample exchange for this command would be:
mimicsh> mimic agent protocol msg IPMI get config {primary_port=623} {secure_port=664} {version=2.0} mimicsh> mimic agent protocol msg IPMI set config primary_port=2623 mimicsh> mimic agent protocol msg IPMI get config {primary_port=2623} {secure_port=664} {version=2.0} -
mimic agent protocol msg IPMI get trace
mimic agent protocol msg IPMI set trace [0 or 1]This command lets the user change the IPMI tracing configuration for an agent. A sample exchange would be:
mimicsh> mimic agent assign 9 mimicsh> mimic agent protocol msg IPMI get trace 0 mimicsh> mimic agent protocol msg IPMI set trace 1 mimicsh> mimic agent protocol msg IPMI get trace 1
and the log would show:INFO - agent 9 trace enabled for IPMI INFO - agent 9 decoded IPMI request INFO - Message 56, Get Channel Authentication Capabilities INFO - SID 0x0 = 0 INFO - Field 1 "Channel Number", len 1-1 INFO - Value: \x8e INFO - 1....... = "get IPMI v2.0+ extended data" INFO - ....1110 = "retrieve information for channel this request was issued on" INFO - Field 2 "Requested Maximum Privilege Level", len 1-1 INFO - Value: \x04 = "Administrator level" INFO - agent 9 simulated IPMI response INFO - Message 56, Get Channel Authentication Capabilities INFO - SID 0x0 = 0 INFO - Field 1 "Completion Code", len 1-1 INFO - Value: \x00 = "UNKNOWN" INFO - Field 2 "Channel Number", len 1-1 INFO - Value: \x01 INFO - Field 3 "Authentication Type Support", len 1-1 INFO - Value: \x97 INFO - 1....... = "IPMI v2.0+ extended capabilities" INFO - .0...... INFO - ..0..... INFO - ...1.... = "straight password / key" INFO - ....0... INFO - .....1.. = "MD5" INFO - ......1. = "MD2" INFO - .......1 = "none" INFO - Field 4 "Authentication Type Support", len 1-1 INFO - Value: \x04 INFO - 0....... INFO - .0...... INFO - ..0..... = "KG is set to default (all 0's)" INFO - ...0.... INFO - ....0... INFO - .....1.. = "Non-null usernames enabled" INFO - ......0. INFO - .......0 INFO - Field 5 "Extended Capabilities", len 1-1 INFO - Value: \x0a INFO - ......1. = "channel supports IPMI v2.0 connections" INFO - .......0 INFO - Field 6 "OEM ID", len 3-3 INFO - Value: \x00 00 00 INFO - Field 7 "OEM auxiliary data", len 1-1 INFO - Value: \x00 ...
-
mimic protocol msg IPMI get stats_hdr
mimic agent protocol msg IPMI get statisticsReturns IPMI statistics information:
- a list of statistic headers, and
- current statistics values for the specified server.
In order, the statistic values are:
- Total number of connections established.
- Total number of disconnects.
- Total number of received commands.
- Total number of "too short" errors.
- Total number of "unrecognized" errors (IANA enterprise, message type, etc).
- Total number of invalid authentications.
- Total number of bad session IDs.
- Total number of authentication failures.
- Total number of SOL requests dropped (not implemented).
- Total number of OEM payloads dropped.
- Total number of bad sequence numbers.
- Total number of received responses which are dropped.
- Total number of dropped commands due to unknown NETFN.
- Total number of dropped commands due to unknown command.
- Total number of dropped commands due to bad syntax.
- Total number of dropped commands due to bad simulation.
A sample exchange for these commands would be:
mimicsh> mimic protocol msg IPMI get stats_hdr {{connect} {Connect}} {{disconnect} {Disconnect}} {{received} {Received}} {{tooshort} {TooShort}} {{unrecognized} {Unrecognized}} {{invalidauth} {InvalidAuth}} {{badsessionid} {BadSessionID}} {{authfail} {AuthFail}} {{droppedsol} {SerialOverLAN}} {{droppedoem} {OEMPayload}} {{badseq} {BadSequence}} {{droppedrsp} {Response}} {{droppednetfn} {NETFN}} {{unknowncmd} {Unknown}} {{badparse} {BadParse}} {{badsim} {SimError}} mimicsh> mimic agent protocol msg IPMI get statistics 0 0 7 0 0 0 0 0 0 0 0 0 0 0 0 0 -
mimic agent protocol msg IPMI get attr
mimic agent protocol msg IPMI set attr valuewhere attr is one of the following:
- working_authtype - the current authentication type
- session_id - the current session ID
- outbound_seq - the current outbound sequence number
- inbound_seq - the current inbound sequence number
- field N - the value of the N-th field in the request
These are useful in action scripts.
-
mimic protocol msg IPMI get args
-
Message Dictionary
All IPMI messages known to MIMIC are defined in the message dictionary config/ipmi/messages.cfg in the uniform MIMIC configuration file syntax. For example, this file contains:
version = 8.00 global = { } # Chassis include = { file = netfn_00.cfg } # App include = { file = netfn_06.cfg } # Storage include = { file = netfn_0a.cfg }and netfn_06.cfg containsnetfn = { id = 6 number = \x06 name = App reference = Intelligent Platform Management Interface Specification Second Generation v2.0 Document Revision 1.0 February 12, 2004 May 5, 2005 Markup # Global Commands include = { file = msg_06_01.cfg } include = { file = msg_06_02.cfg } include = { file = msg_06_03.cfg } include = { file = msg_06_04.cfg } include = { file = msg_06_05.cfg } include = { file = msg_06_06.cfg } include = { file = msg_06_07.cfg } include = { file = msg_06_08.cfg } # IPMI Messaging Support Commands include = { file = msg_06_37.cfg } include = { file = msg_06_38.cfg } include = { file = msg_06_39.cfg } include = { file = msg_06_3a.cfg } ...The dictionary basically comprises a hierarchical tree of configuration files, one for each known message. In each message configuration file, the request and response blocks for the defined command list the fields they contain, including their types, values, etc. For example, the msg_06_38.cfg file contains:message = { id = 56 number = \x38 name = Get Channel Authentication Capabilities reference = 22.13 request = { field = { id = 1 byte = 1 name = Channel Number length = 1 type = bits bit = { offset = 7 on = get IPMI v2.0+ extended data } bit = { offset = 3-0 enum = { value = \xe name = retrieve information for channel this request was issued on } } } field = { id = 2 byte = 2 name = Requested Maximum Privilege Level length = 1 type = enum enum = { value = 0 name = reserved } enum = { value = 1 name = Callback level } enum = { value = 2 name = User level } enum = { value = 3 name = Operator level } enum = { value = 4 name = Administrator level } enum = { value = 5 name = OEM Proprietary level } } } response = { field = { id = 1 byte = 1 name = Completion Code length = 1 type = enum } field = { id = 2 byte = 2 name = Channel Number length = 1 type = number } field = { id = 3 byte = 3 name = Authentication Type Support length = 1 type = bits bit = { offset = 7 enum = { value = 1 name = IPMI v2.0+ extended capabilities } enum = { value = 0 name = IPMI v1.5 support only } } bit = { offset = 6 on = reserved } bit = { offset = 5 on = OEM proprietary } bit = { offset = 4 on = straight password / key } bit = { offset = 3 on = reserved } bit = { offset = 2 on = MD5 } bit = { offset = 1 on = MD2 } bit = { offset = 0 on = none } } field = { id = 4 byte = 4 name = Authentication Type Support length = 1 type = bits bit = { offset = 7 on = reserved } bit = { offset = 6 on = reserved } bit = { offset = 5 enum = { value = 1 name = KG is set to non-zero value. } enum = { value = 0 name = KG is set to default (all 0's) } } bit = { offset = 4 on = Per-message Authentication is disabled } bit = { offset = 3 on = User Level Authentication is disabled } bit = { offset = 2 on = Non-null usernames enabled } bit = { offset = 1 on = Null usernames enabled } bit = { offset = 0 on = Anonymous Login enabled } } field = { id = 5 byte = 5 name = Extended Capabilities version = 2.0 length = 1 type = bits bit = { offset = 1 on = channel supports IPMI v2.0 connections } bit = { offset = 0 on = channel supports IPMI v1.5 connections } } field = { id = 6 byte = 6 name = OEM ID length = 3 type = octets } field = { id = 7 byte = 9 name = OEM auxiliary data length = 1 type = octets } } } -
IPMI Proxy
The IPMI Proxy (ipmiproxy) is a stand-alone utility to record IPMI sessions and create basic IPMI simulations. The proxy sits between the IPMI management application and the target device, recording requests and responses into a walkfile, which can then be fed to the IPMI Recorder to create the simulation. To achieve the recording, the IPMI management applications needs to query the IPMI Proxy address instead of the target.
The following command line options are supported:
-
--target ip-address
mandatory command line argument to specify the target device supporting IPMI commands. -
--remote remote-port
optional command line argument to specify the port number on the target device to send IPMI requests to. By default this will be the standard port 623. -
--local local-port
optional command line argument to specify the port number on proxy on which to accept IPMI requests from the management application. By default this will be the standard port 623. This option is specially useful if ipmiproxy is run as non-root, because you will get a permission failure trying to open the default port 623. -
--authcode authentication-code
mandatory command line argument to specify the password to access the target device. -
--transform transform-file
optional command line argument to specify a transform file, which will transform certain messages. This is useful to force IPMI v1.5 communication, when the device and/or application support either. -
--walkfiledir directory
optional command line argument to specify a different walkfile directory. The default is /tmp. -
--walkfile filename
optional command line argument to specify a different walkfile filename. The default is ipmiwalk-IP-ADDRESS. -
--app-cipher cipher-suite
the cipher suite to use to communicate with this proxy. Use --app-cipher --help to list the available ciphers. -
--trg-cipher cipher-suite
the cipher suite to use to communicate with the target. Use --trg-cipher --help to list the available ciphers. -
--password
the password to use (required) -
--kgkey
the kgkey to use (optional)
For example, assuming the target device is at 10.0.0.1, the following are the command lines for the different cipher suites:
% ./ipmiproxy --target 10.0.0.1 --local 6623 --app-cipher 0 --password admin123 % ./ipmiproxy --target 10.0.0.1 --local 6623 --app-cipher 1 --password admin123
-
-
IPMI Recorder
The IPMI Recorder (ipmirec) is a stand-alone utility to record IPMI sessions and create basic IPMI simulations. The recorder queries the target device, recording requests and responses into a walkfile and creating the simulation.
The IPMI Recorder can run in either live or file mode. In live mode, the Recorder interacts with a running target device on your network in real time using the IPMI protocol. In the discovery phase, the Recorder queries the target device according to the configuration file config/ipmi/discover.cfg, and stores the requests and responses in a walkfile. In the second simulation phase, the Recorder creates the simulation from the discovered commands.
The file mode works by reading a walkfile created previously either by hand or from a previous run of the Recorder against a Live target device.
Once data is captured from a device, the MIMIC Agent Simulator can use the simulation generated by the IPMI Recorder to simulate the device realistically. Any variation on this basic simulation can later be done for use with the Simulator.
The following command line options are supported:
-
--target ip-address
mandatory command line argument to specify the target device to query in "live mode" via the IPMI protocol. -
--port remote-port
optional command line argument to specify the port number on the target device to send IPMI requests to. By default this will be the standard port 623. -
--file walkfile
mandatory command line argument to specify the input walkfile for "file mode" described above. -
--simulation simulation-name
This specifies the simulation name of the existing SNMP simulation to store the IPMI simulation.
-
--scenario scenario-name
This specifies a scenario name. The SNMP scenario with the same name has to already exist.
-
--walkfiledir directory
optional command line argument to specify a different walkfile directory. The default is /tmp. -
--walkfile filename
optional command line argument to specify a different walkfile filename. The default is ipmiwalk-IP-ADDRESS.
-
-
Interoperability
-
IPMITOOL
The IPMI modules has been tested for interoperability with IPMITOOL 1.8.10. ipmitool currently uses cipher suite 3 as the default. In particular, the following shows that RMCP+ cipher suites 0 through 3 interoperate:
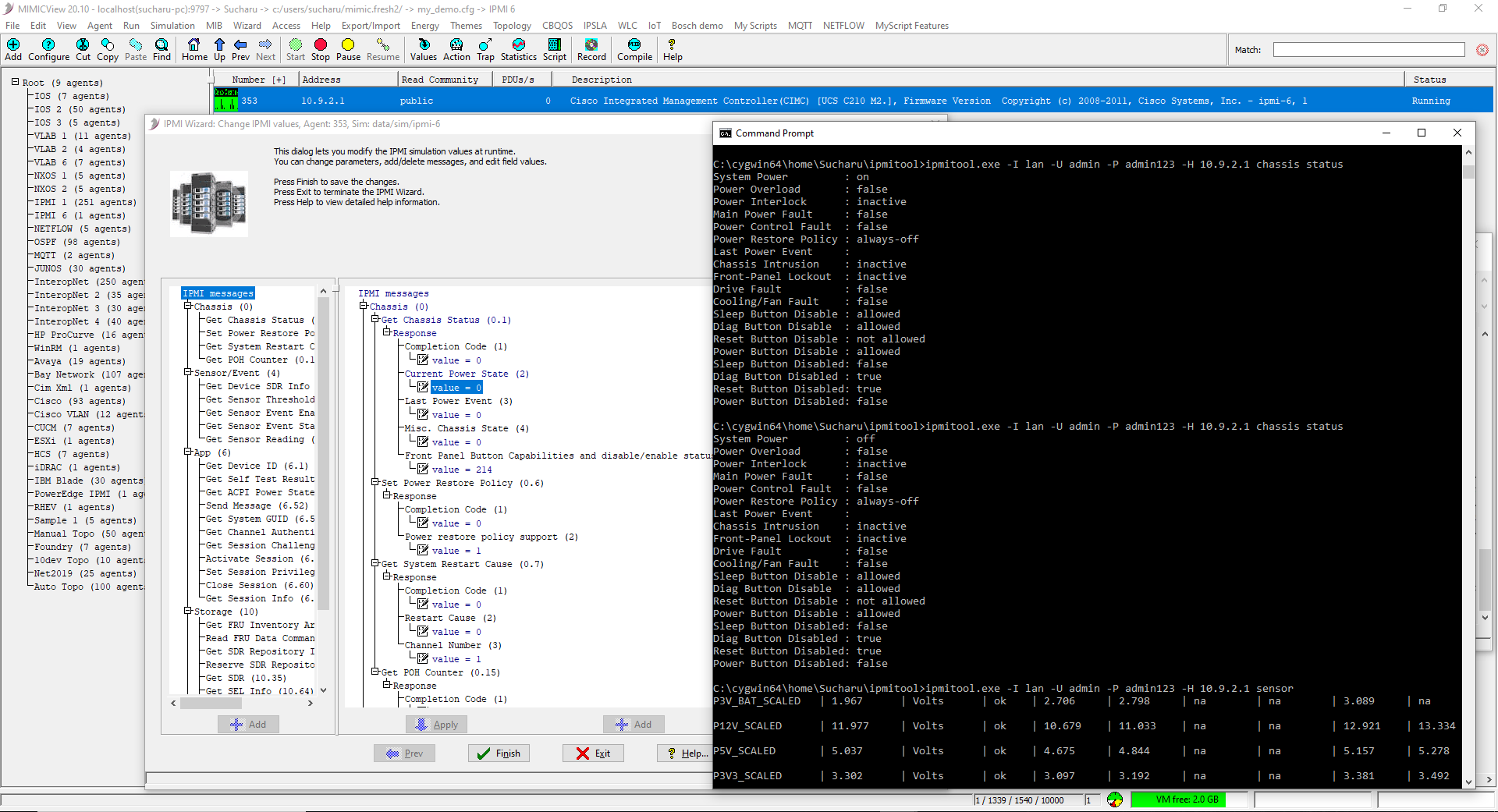
% ./ipmitool -I lanplus -H 10.0.0.1 -v -C 0 -U admin -P admin123 -A password chassis status System Power : off Power Overload : false Power Interlock : inactive Main Power Fault : false Power Control Fault : false Power Restore Policy : always-off Last Power Event : Chassis Intrusion : inactive Front-Panel Lockout : inactive Drive Fault : false Cooling/Fan Fault : false Sleep Button Disable : not allowed Diag Button Disable : allowed Reset Button Disable : not allowed Power Button Disable : allowed Sleep Button Disabled: false Diag Button Disabled : true Reset Button Disabled: false Power Button Disabled: true % ./ipmitool -I lanplus -H 10.0.0.1 -v -C 1 -U admin -P admin123 -A password chassis status System Power : off Power Overload : false Power Interlock : inactive Main Power Fault : false Power Control Fault : false Power Restore Policy : always-off Last Power Event : Chassis Intrusion : inactive Front-Panel Lockout : inactive Drive Fault : false Cooling/Fan Fault : false Sleep Button Disable : not allowed Diag Button Disable : allowed Reset Button Disable : not allowed Power Button Disable : allowed Sleep Button Disabled: false Diag Button Disabled : true Reset Button Disabled: false Power Button Disabled: true % ./ipmitool -I lanplus -H 10.0.0.1 -v -C 2 -U admin -P admin123 -A password chassis status System Power : off Power Overload : false Power Interlock : inactive Main Power Fault : false Power Control Fault : false Power Restore Policy : always-off Last Power Event : Chassis Intrusion : inactive Front-Panel Lockout : inactive Drive Fault : false Cooling/Fan Fault : false Sleep Button Disable : not allowed Diag Button Disable : allowed Reset Button Disable : not allowed Power Button Disable : allowed Sleep Button Disabled: false Diag Button Disabled : true Reset Button Disabled: false Power Button Disabled: true % ./ipmitool -I lanplus -H 10.0.0.1 -v -C 3 -U admin -P admin123 -A password chassis status System Power : off Power Overload : false Power Interlock : inactive Main Power Fault : false Power Control Fault : false Power Restore Policy : always-off Last Power Event : Chassis Intrusion : inactive Front-Panel Lockout : inactive Drive Fault : false Cooling/Fan Fault : false Sleep Button Disable : not allowed Diag Button Disable : allowed Reset Button Disable : not allowed Power Button Disable : allowed Sleep Button Disabled: false Diag Button Disabled : true Reset Button Disabled: false Power Button Disabled: true
or on Windows:
-
IPMIUTIL
The IPMI modules has been tested for interoperability with IPMIUTIL 2.91. In particular, the following shows that RMCP+ cipher suite 6 interoperates:
% ./ipmiutil sensor -N 10.0.0.1 -U admin -P admin123 -V 4 -T 2 -J 6 ipmiutil ver 2.91 isensor: version 2.91 Opening lanplus connection to node 10.0.0.1 ... Connected to node 10.0.0.1 -- BMC version 2.10, IPMI version 2.0 _ID_ SDR_Type_xx ET Own Typ S_Num Sens_Description Hex & Interp Reading 0001 SDR Full 01 01 20 a 01 snum 01 Temp = 49 OK -55.00 degrees C 0002 SDR Full 01 01 20 a 01 snum 02 Temp = 4c OK -52.00 degrees C 0003 SDR Full 01 01 20 a 01 snum 05 Temp = a8 OK 40.00 degrees C 0004 SDR Full 01 01 20 a 01 snum 06 Temp = a8 OK 40.00 degrees C 0005 SDR Full 01 01 20 a 01 snum 08 Ambient Temp = 98 OK 24.00 degrees C 0006 SDR Comp 02 6f 20 a 29 snum 10 CMOS Battery = 0000 OK 0007 SDR Comp 02 6f 20 a 29 snum 11 ROMB Battery = 0000 OK 0008 SDR Comp 02 03 20 a 02 snum 12 VCORE = 0001 OK 0009 SDR Comp 02 03 20 a 02 snum 13 VCORE = 0001 OK 000a SDR Comp 02 03 20 a 02 snum 16 CPU VTT = 0001 OK 000b SDR Comp 02 03 20 a 02 snum 17 1.5V PG = 0001 OK 000c SDR Comp 02 03 20 a 02 snum 18 1.8V PG = 0001 OK 000d SDR Comp 02 03 20 a 02 snum 19 3.3V PG = 0001 OK 000e SDR Comp 02 03 20 a 02 snum 1a 5V PG = 0001 OK 000f SDR Comp 02 03 20 a 02 snum 1b 1.5V PXH PG = 0001 OK 0010 SDR Comp 02 03 20 a 02 snum 1c 5V Riser PG = 0001 OK 0011 SDR Comp 02 03 20 a 02 snum 1d Backplane PG = 0001 OK 0012 SDR Comp 02 03 20 a 02 snum 20 Linear PG = 0001 OK 0013 SDR Comp 02 03 20 a 02 snum 21 0.9V PG = 0001 OK 0014 SDR Comp 02 03 20 a 02 snum 22 0.9V Over Volt = 0001 OK 0015 SDR Comp 02 03 20 a 02 snum 23 CPU Power Fault = 0001 OK 0016 SDR Full 01 01 20 a 04 snum 30 FAN 1 RPM = 71 OK 8475.00 RPM 0017 SDR Full 01 01 20 a 04 snum 31 FAN 2 RPM = 6e OK 8250.00 RPM 0018 SDR Full 01 01 20 a 04 snum 32 FAN 3 RPM = 6f OK 8325.00 RPM 0019 SDR Full 01 01 20 a 04 snum 33 FAN 4 RPM = 6d OK 8175.00 RPM 001a SDR Full 01 01 20 a 04 snum 34 FAN 5 RPM = 38 OK 4200.00 RPM 001b SDR Full 01 01 20 a 04 snum 35 FAN 6 RPM = 38 OK 4200.00 RPM 001c SDR Comp 02 6f 20 a 25 snum 50 Presence = 0001 OK* 001d SDR Comp 02 6f 20 a 25 snum 51 Presence = 0001 OK* 001e SDR Comp 02 6f 20 a 25 snum 54 Presence = 0001 OK* 001f SDR Comp 02 6f 20 a 25 snum 55 Presence = 0001 OK* 0020 SDR Comp 02 6f 20 a 25 snum 56 Presence = 0001 OK* 0021 SDR Comp 02 6f 20 a 25 snum 57 Presence = 0001 OK* 0022 SDR Comp 02 6f 20 a 1b snum 59 DRAC5 Conn 2 Cbl = 0001 _ 0023 SDR Comp 02 03 20 a 02 snum 5f PFault Fail Safe = 0000 Absent 0024 SDR Comp 02 6f 20 a 07 snum 60 Status = 0080 ProcPresent 0025 SDR Comp 02 6f 20 a 07 snum 61 Status = 0080 ProcPresent 0026 SDR Comp 02 6f 20 a 08 snum 64 Status = 0001 Present 0027 SDR Comp 02 6f 20 a 08 snum 65 Status = 0001 Present 0028 SDR Comp 02 6f 20 a 1b snum 66 Status = 0001 _ 0029 SDR Comp 02 6f 20 a 15 snum 70 RAC Status = 0007 OK 002a SDR Comp 02 6f 20 a 23 snum 71 OS Watchdog = 0000 OK 002b SDR Comp 02 6f 20 a 10 snum 72 SEL = 0000 Absent 002c SDR Comp 02 6f 20 a 05 snum 73 Intrusion = 0000 OK 002d SDR Comp 02 0b 20 a 08 snum 74 PS Redundancy = 0001 Present 002e SDR Comp 02 0b 20 a 04 snum 75 Fan Redundancy = 0001 Redundant 002f SDR Comp 02 03 20 m 01 snum 76 CPU Temp Interf = 0040 NotAvailable 0030 SDR Comp 02 6f 20 a 0d snum 80 Drive = 0001 Unused Faulty 0031 SDR Comp 02 6f 20 a 1b snum 90 Cable SAS A = 0001 _ 0032 SDR Comp 02 6f 20 a 1b snum 91 Cable SAS B = 0001 _ 0033 SDR Full 01 01 20 a 03 snum 94 Current 1 = 00 Absent 0.00 na 0034 SDR Full 01 01 20 a 03 snum 95 Current 2 = 00 Absent 0.00 na 0035 SDR Full 01 01 20 a 02 snum 96 Voltage 1 = 00 Absent 0.00 na 0036 SDR Full 01 01 20 a 02 snum 97 Voltage 2 = 00 Absent 0.00 na 0037 SDR Full 01 01 20 a 03 snum 98 System Level = 00 Absent 0.00 na 0038 SDR Comp 02 6f 20 a c0 snum 99 Power Optimized = 0000 Absent 0039 SDR EntA 08 10 07 01 c0: 03 01 03 02 0a 01 0a 02 003a SDR IPMB 12 0e dev: 20 00 df 07 01 BMC 003b SDR IPMB 12 11 dev: 26 00 38 0b 01 DRAC 5 003c SDR FRU 11 17 dev: 20 00 80 00 07 01 System Board 003d SDR FRU 11 0f dev: 20 b0 02 00 03 01 CPU1 003e SDR FRU 11 0f dev: 20 b0 02 00 03 02 CPU2 003f SDR FRU 11 12 dev: 20 02 80 00 1a 03 Storage 0040 SDR FRU 11 0f dev: 20 03 80 00 0a 01 PS 1 0041 SDR FRU 11 0f dev: 20 04 80 00 0a 02 PS 2 0042 SDR FRU 11 12 dev: 20 05 80 00 1a 01 Storage 0043 SDR FRU 11 11 dev: 26 00 80 00 0b 01 DRAC 5 0044 SDR FRU 11 10 dev: 20 b0 02 00 10 01 Riser 0045 SDR FRU 11 14 dev: 20 b0 02 00 10 02 Sideplane 0046 SDR Comp 02 6f b1 a 0c snum 01 ECC Corr Err = 0000 Unknown 0047 SDR Comp 02 6f b1 a 0c snum 02 ECC Uncorr Err = 0000 Unknown 0048 SDR Comp 02 6f b1 a 13 snum 03 I/O Channel Chk = 0000 Unknown ipmiutil sensor, completed successfully -
FREEIPMI
The IPMI modules has been tested for interoperability with FREEIPMI 1.6.3:
% ./ipmi-chassis -D LAN_2_0 -h 10.0.0.9 -I 0 -u "admin" -p "admin123" --get-chassis-status System Power : on Power overload : false Interlock : inactive Power fault : false Power control fault : false Power restore policy : Always off Last Power Event : unknown Chassis intrusion : inactive Front panel lockout : inactive Drive Fault : false Cooling/fan fault : false Power off button : enabled Reset button : disabled Diagnostic Interrupt button : disabled Standby button : enabled Power off button disable : allowed Reset button disable : unallowed Diagnostic interrupt button disable : allowed Standby button disable : allowed % ./ipmi-chassis -D LAN_2_0 -h 10.0.0.9 -I 1 -u "admin" -p "admin123" --get-chassis-status System Power : on Power overload : false Interlock : inactive Power fault : false Power control fault : false Power restore policy : Always off Last Power Event : unknown Chassis intrusion : inactive Front panel lockout : inactive Drive Fault : false Cooling/fan fault : false Power off button : enabled Reset button : disabled Diagnostic Interrupt button : disabled Standby button : enabled Power off button disable : allowed Reset button disable : unallowed Diagnostic interrupt button disable : allowed Standby button disable : allowed % ./ipmi-chassis -D LAN_2_0 -h 10.0.0.9 -I 2 -u "admin" -p "admin123" --get-chassis-status System Power : on Power overload : false Interlock : inactive Power fault : false Power control fault : false Power restore policy : Always off Last Power Event : unknown Chassis intrusion : inactive Front panel lockout : inactive Drive Fault : false Cooling/fan fault : false Power off button : enabled Reset button : disabled Diagnostic Interrupt button : disabled Standby button : enabled Power off button disable : allowed Reset button disable : unallowed Diagnostic interrupt button disable : allowed Standby button disable : allowed % ./ipmi-chassis -D LAN_2_0 -h 10.0.0.9 -I 3 -u "admin" -p "admin123" --get-chassis-status System Power : on Power overload : false Interlock : inactive Power fault : false Power control fault : false Power restore policy : Always off Last Power Event : unknown Chassis intrusion : inactive Front panel lockout : inactive Drive Fault : false Cooling/fan fault : false Power off button : enabled Reset button : disabled Diagnostic Interrupt button : disabled Standby button : enabled Power off button disable : allowed Reset button disable : unallowed Diagnostic interrupt button disable : allowed Standby button disable : allowed % ./ipmi-chassis -D LAN_2_0 -h 10.0.0.9 -I 6 -u "admin" -p "admin123" --get-chassis-status System Power : on Power overload : false Interlock : inactive Power fault : false Power control fault : false Power restore policy : Always off Last Power Event : unknown Chassis intrusion : inactive Front panel lockout : inactive Drive Fault : false Cooling/fan fault : false Power off button : enabled Reset button : disabled Diagnostic Interrupt button : disabled Standby button : enabled Power off button disable : allowed Reset button disable : unallowed Diagnostic interrupt button disable : allowed Standby button disable : allowed
-
-
Limitations
The current version has these limitations:
- cipher suites 0,1,2,3,6 (section 22.15.2) are supported; others will be added in the future.