MIMIC WEB Module Compatibility
The MIMIC WEB Module is an optional facility that simulates WEB services. This section details interoperability of MIMIC WEB Simulator with a small set of third-party WEB applications to illustrate the different API types (SOAP, XML, REST, WBEM, WS-MAN, Redfish, ...).
-
Table of Contents
-
Windows Management Instrumentation (WMI)
Web Based Enterprise Management (WBEM) is an architecture for managing systems using Web services (Wikipedia). The architecture contains many components (databases, query languages, protocols, and software implementations), some of which are exported through interfaces that MIMIC Web Simulator can simulate.
Windows Management Instrumentation (WMI) is the Microsoft implementation of WBEM, as detailed in this Microsoft page. MIMIC does not currently support the Microsoft-proprietary DCOM access, but the open WinRM API based on WS-MAN and accessible also with Openwsman. This Microsoft page about Windows Remote Management and WMI further details the WinRM API, with database-like operations available in the Microsoft WMI Query Language (WQL).
You can install an optional package with Wizards->Update in MIMICview to run a basic WinRM simulation to interoperate with WinRM.
-
Cisco Unified Communications Manager (CUCM)
The Cisco Unified Communications Manager (CUCM) and Hosted Collaboration Solution (HCS) simulation downloadable with Wizard->Update in MIMICview simulates a Cisco C210 UCS server with VOIP phones and collaboration applications.
We have tested this simulation with Cisco Prime Collaboration:
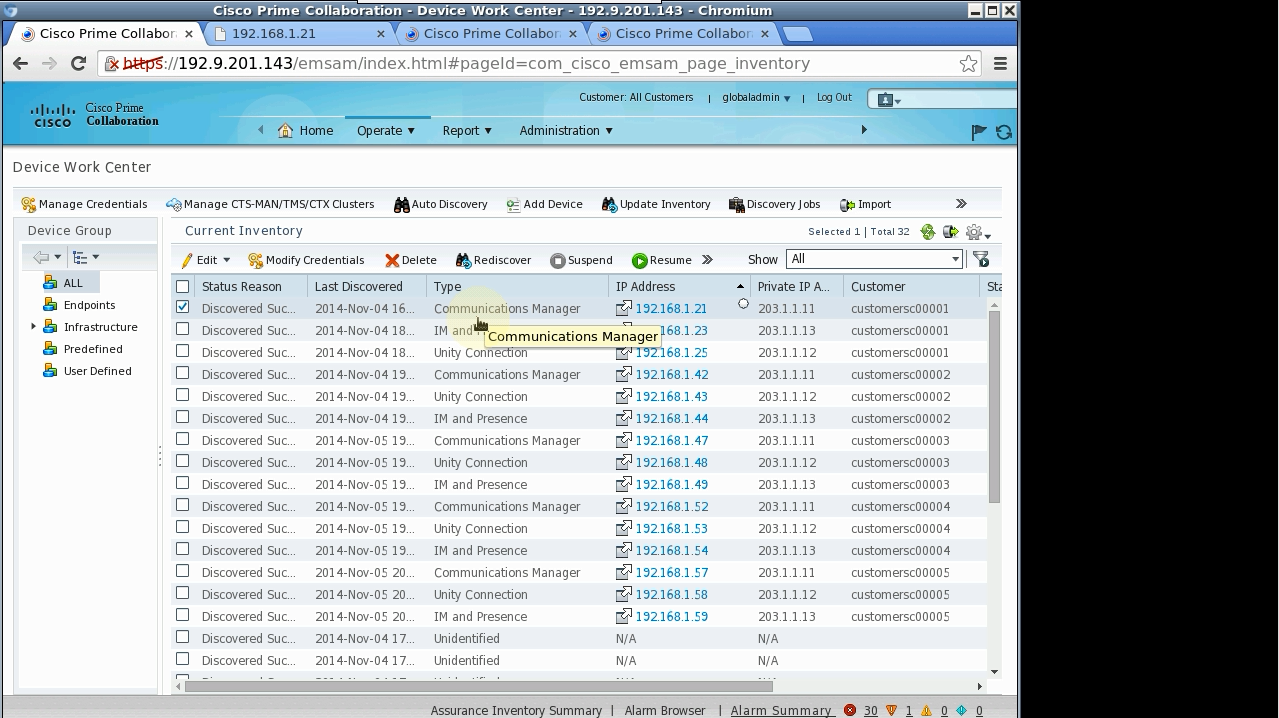
and EMC SMARTS:
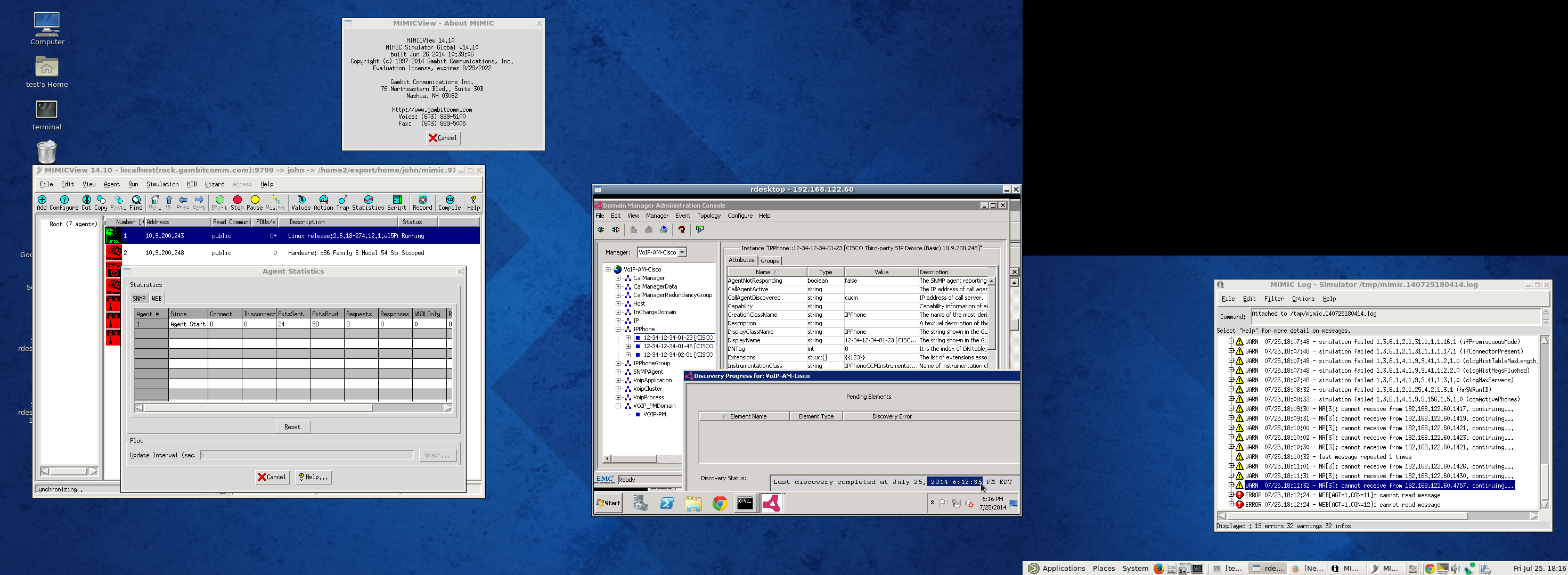
and HPE NNMi:
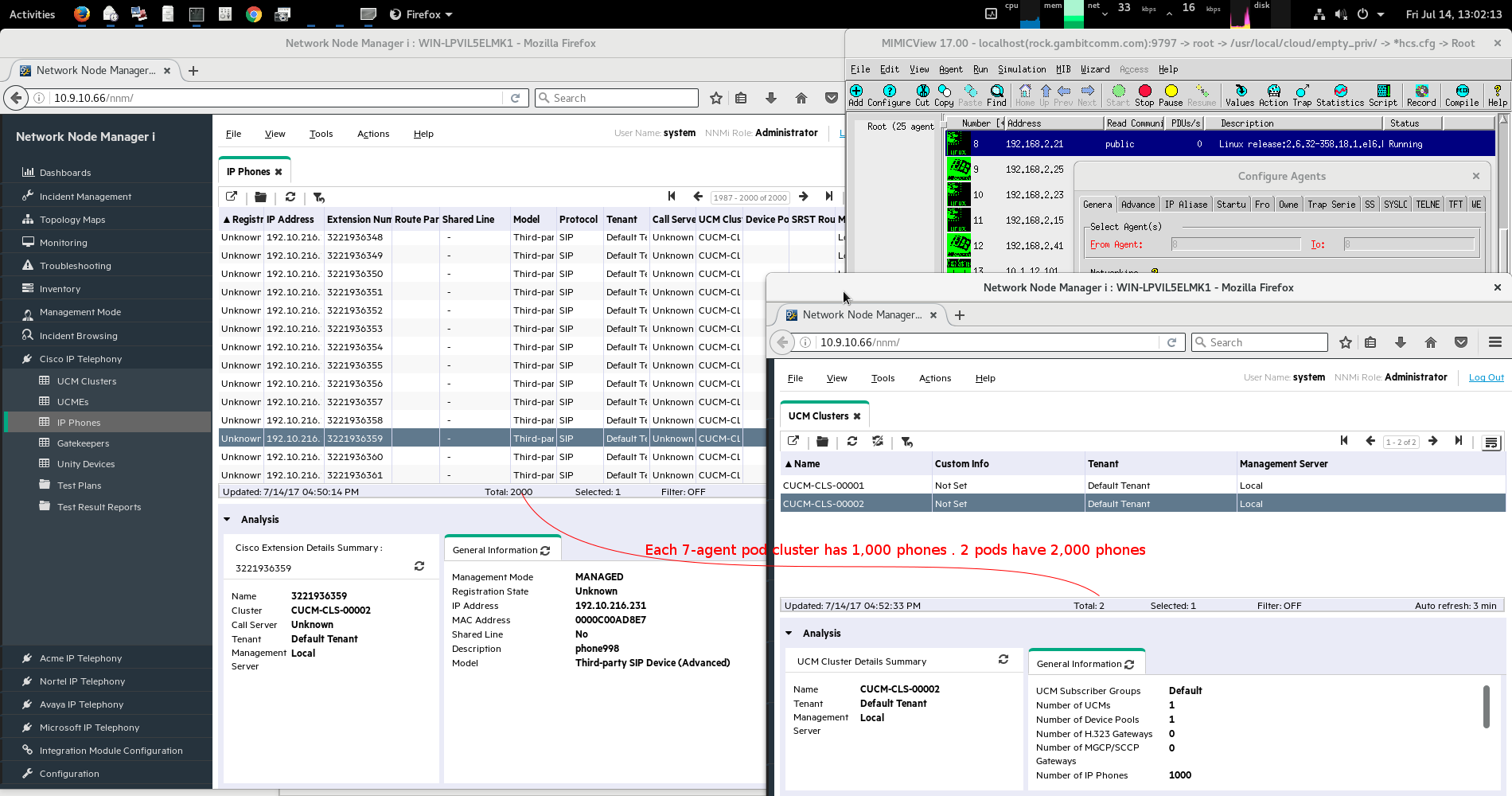
and NetIQ(HP Microfocus) AppManager 8:
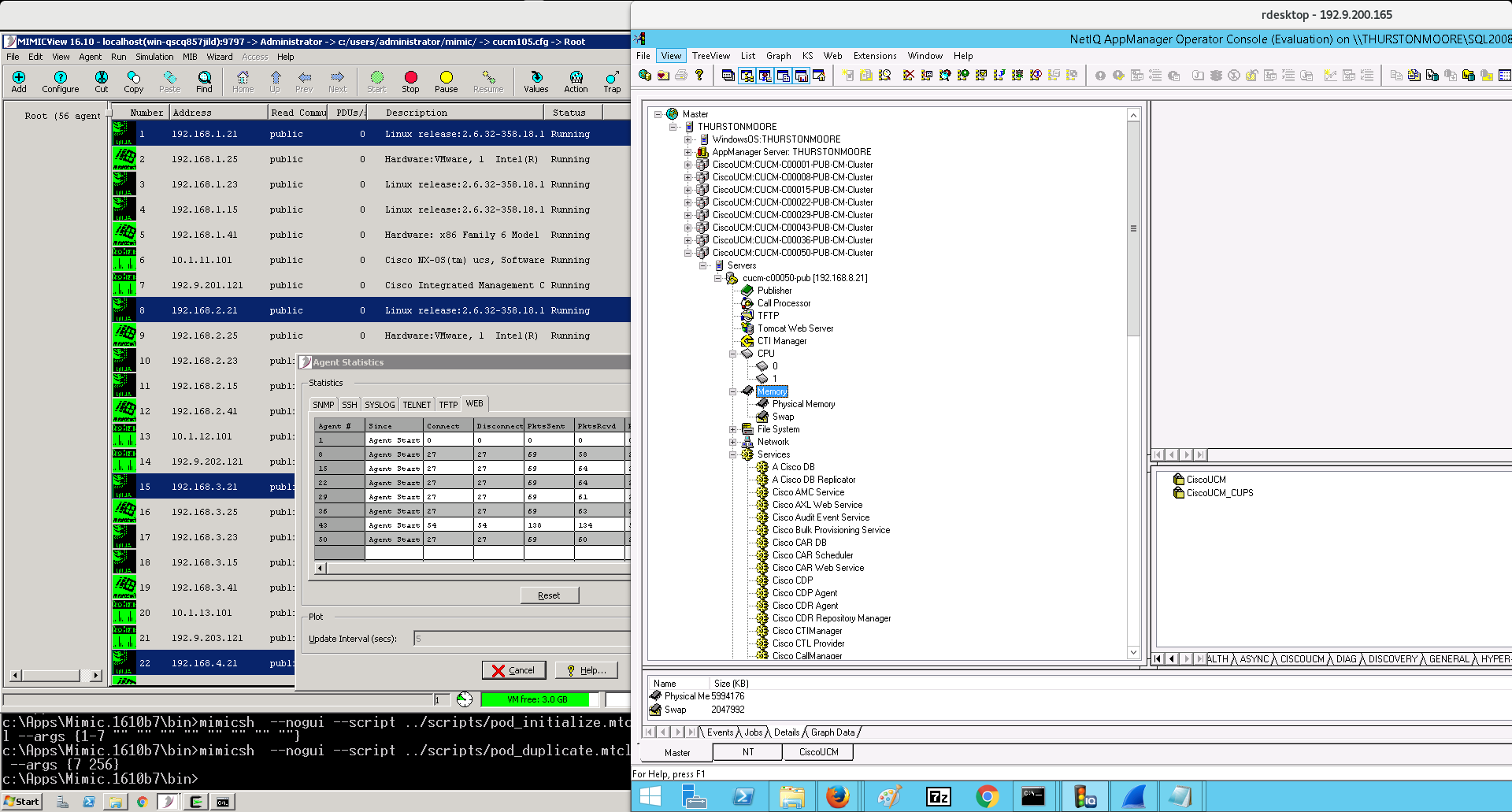
-
VMWare ESXi
The VMware ESXi hypervisor simulation downloadable with Update Wizard has been extensively tested with vSphere Client through the vCenter API
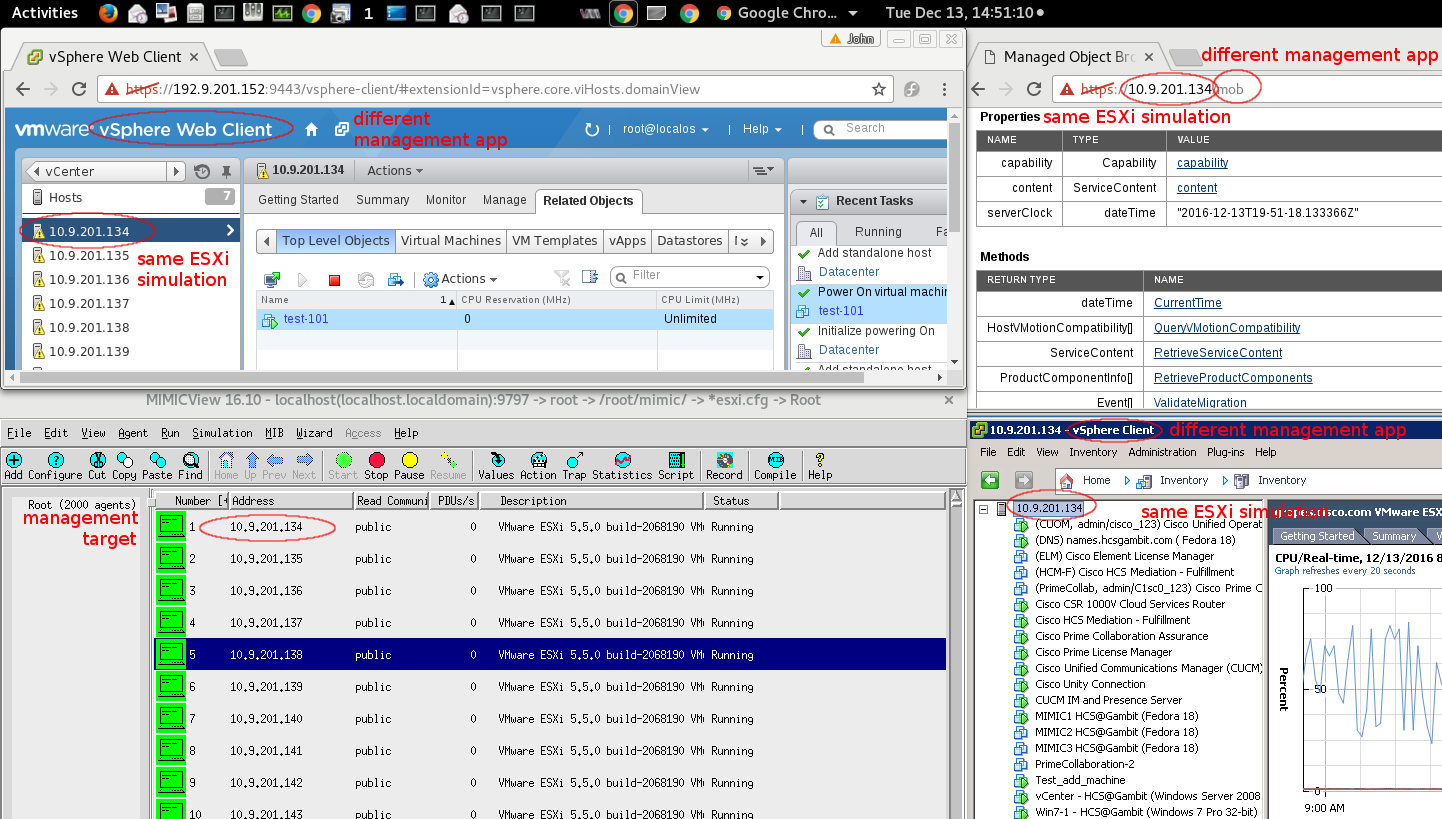
and Hyperglance managing 1000 VMs
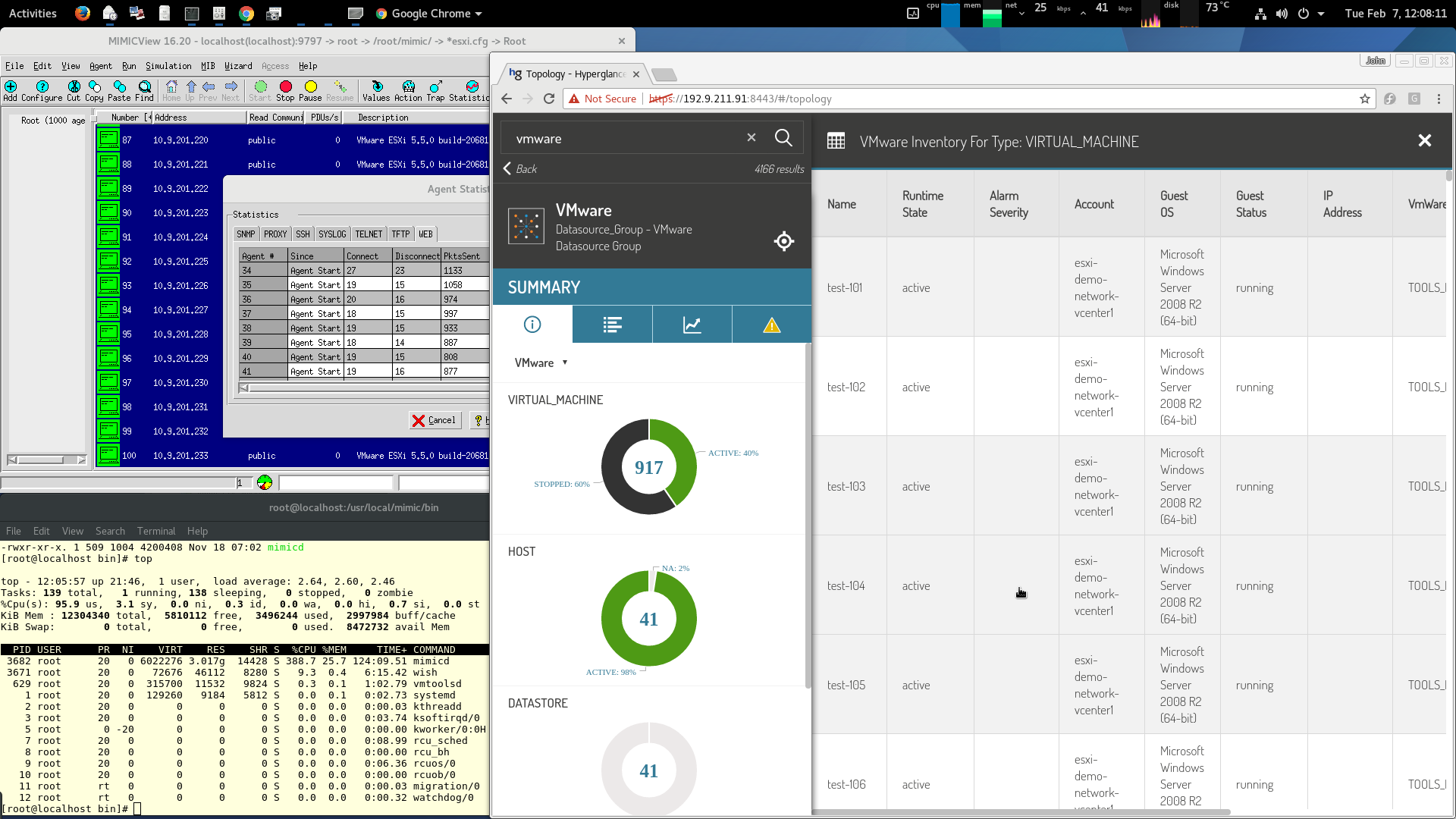
and shown in these videos.
-
Dell iDRAC6 WS-MAN
You can simulate a data center with many simulated Dell iDRAC6 servers and manage them with Dell OpenManage Essentials
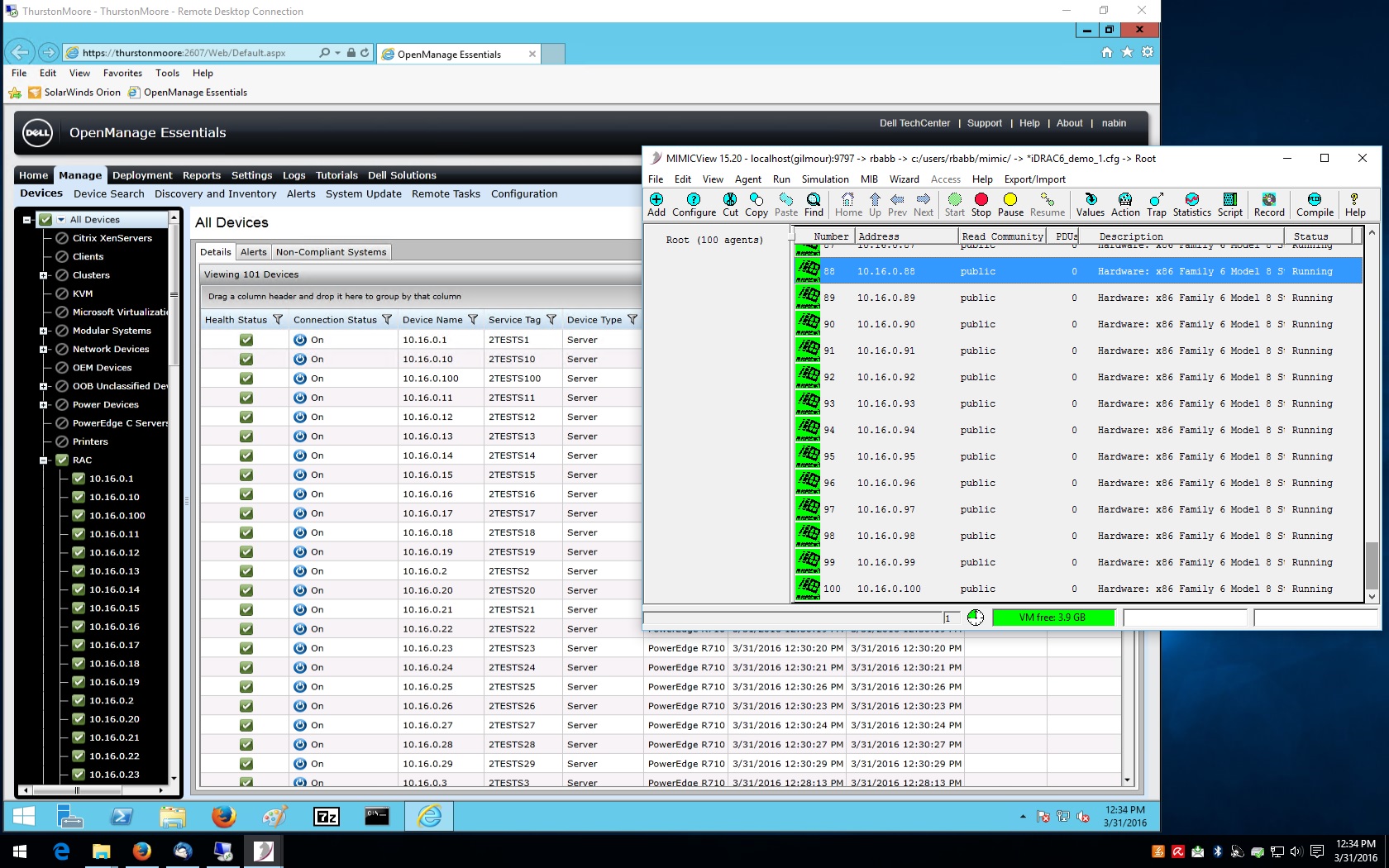
-
Redfish
The MIMIC update package with the Redfish simulation simulates the Redfish management API. This simulation interoperates with redfish-client and Redfishtool.
-
RedHat Enterprise Virtualization
You can install an optional package with Wizards->Update in MIMICview to run the RedHat Enterprise Virtualization server simulation. It interoperates with RHEV-M:
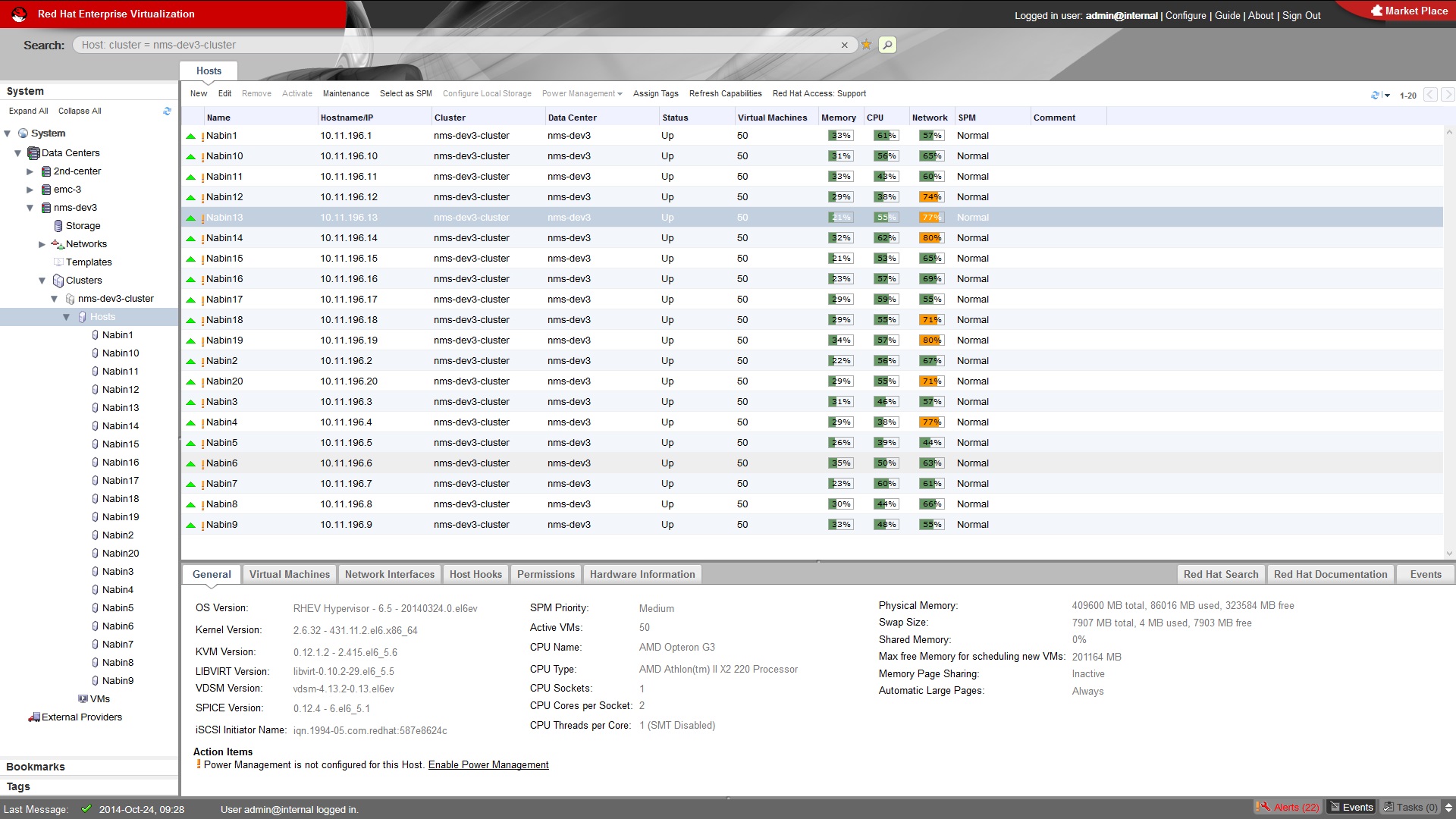
-
Wireshark
To decode HTTPS packets in wireshark, you need to supply the HTTP server private keys for decryption.
-
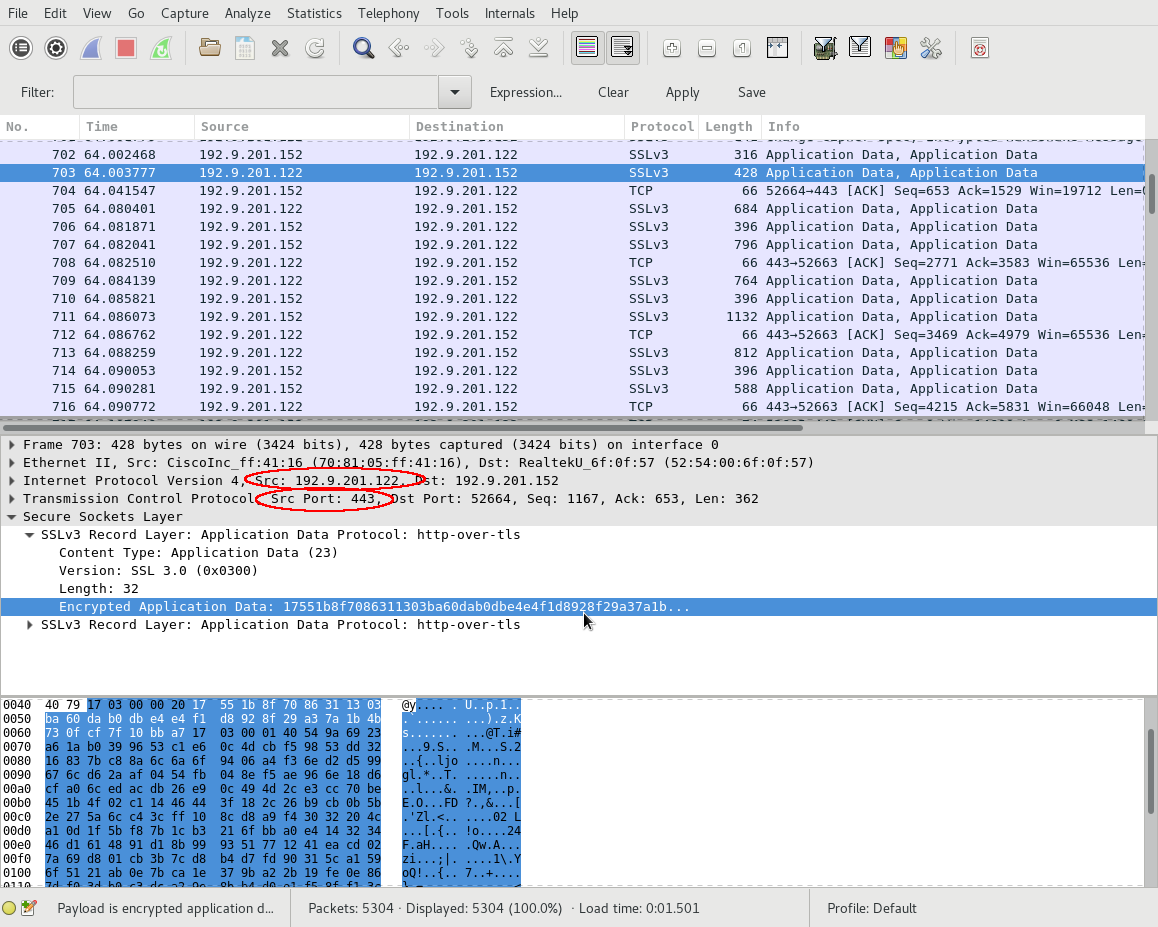
Open the PCAP file of the server-client interaction in Wireshark. The
TLS traffic is encrypted. Identify the server’s IP address
and download the HTTP server side’s TLS private key PEM
file, in this example, SCP to ESXi’s file system to download
/etc/vmware/ssl/rui.key .
The command line to search for private keys in ESXi’s SSH terminal is
[root@localhost:~] find . -name *key* ./etc/ssh/keys-root ./etc/ssh/keys-root/authorized_keys ./etc/ssh/.#ssh_host_dsa_key ./etc/ssh/.#ssh_host_dsa_key.pub ./etc/ssh/.#ssh_host_rsa_key.pub ./etc/ssh/.#ssh_host_rsa_key ./etc/ssh/ssh_host_dsa_key ./etc/ssh/ssh_host_dsa_key.pub ./etc/ssh/ssh_host_rsa_key.pub ./etc/ssh/ssh_host_rsa_key ./etc/vmware/ssl/.#rui.key ./etc/vmware/ssl/rui.key ...
The command line example to SCP download the key is
$ scp root@192.9.201.122:/etc/vmware/ssl/rui.key ~/rui.pem
Identify the TCP port number of the server.
-
For security measures in a production environment, revoke and replace
the server’s TLS key and certificate before giving out the private
key so that the key can not be used to attack the production environment.
-
Use Wireshark’s Edit->Preference->Protocols window
to add the private key.
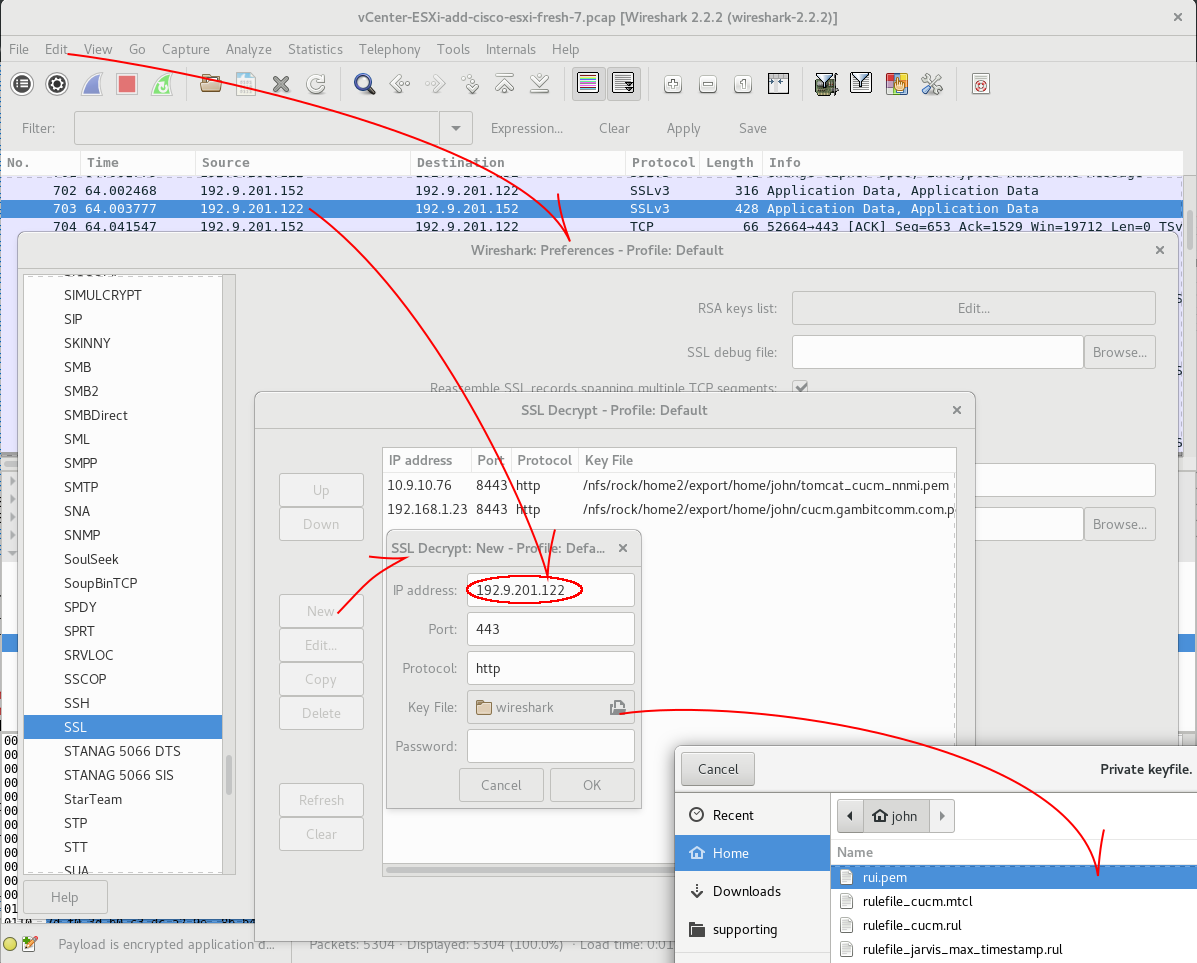
Scroll down to the SSL entry on the left pane, then click New to open the New Profile window, and then click the Key File button to browse your computer’s files and select the downloaded key.
Enter the TCP port number of the server in the New Profile window and enter “http” in the Protocol field.
Click OK to close the browsing window and the preference window.
-
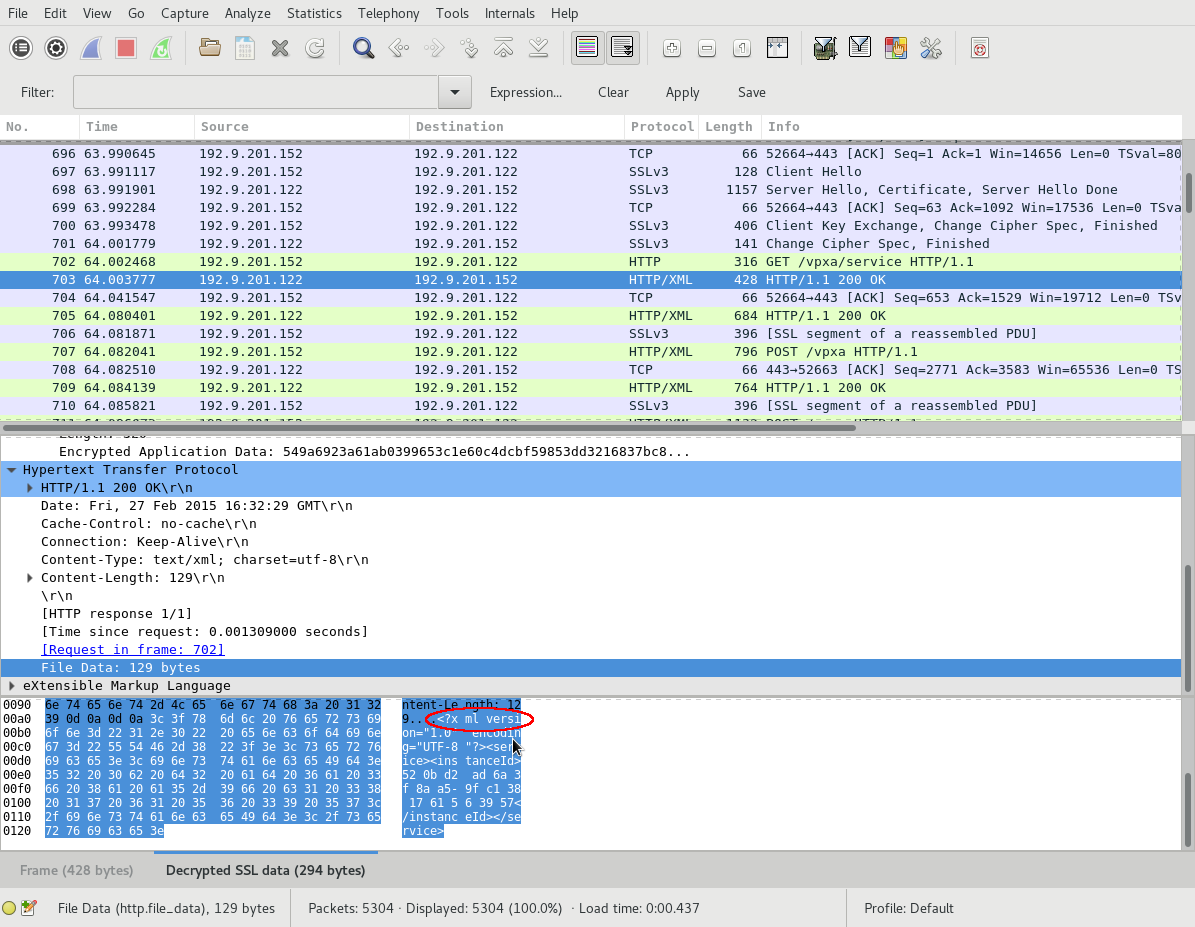
Wireshark automatically applies the decryption, and you can see plain
text XML content.
-
Open the PCAP file of the server-client interaction in Wireshark. The
TLS traffic is encrypted. Identify the server’s IP address
and download the HTTP server side’s TLS private key PEM
file, in this example, SCP to ESXi’s file system to download
/etc/vmware/ssl/rui.key .
